A while back, support for app-based authentication was added for Intune, enabling an app to authenticate and use the Graph API. That’s mentioned in the Intune documentation, along with the steps to create an app. Between that documentation, and the similar Graph documentation, you can figure out how to set up an app. But the whole process might be a little less obvious, so let’s walk through it.
First, we need to create an app. For that, log into https://portal.azure.com and navigate to Azure Active Directory –> App Registrations, then click “+ New registration.” For the name, I’ll specify “Contoso Intune Graph API” for the name. I’m only going to use this app for one tenant, so I’ll choose the single tenant option. And for the web redirect URI, the documentation says to use a type of “Public/native” and a value of “urn:ietf:wg:oauth:2.0:oob”. So you end up with something that looks like this:
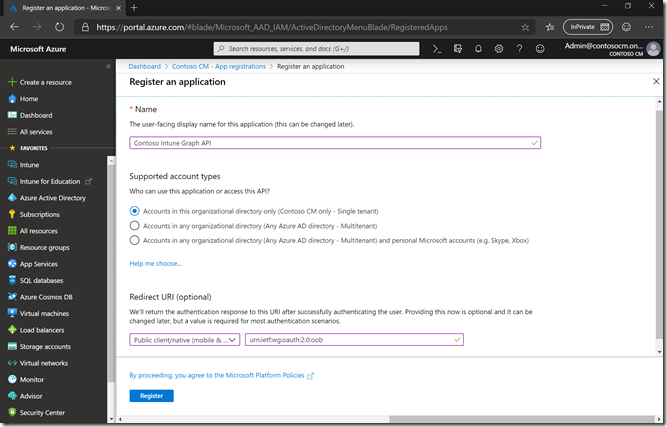
After clicking Register, we can then see the app details:
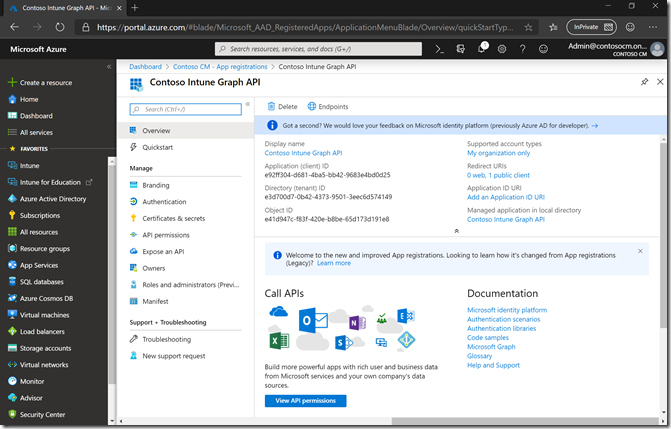
Next, click “API permissions” and then “Add a permission”:
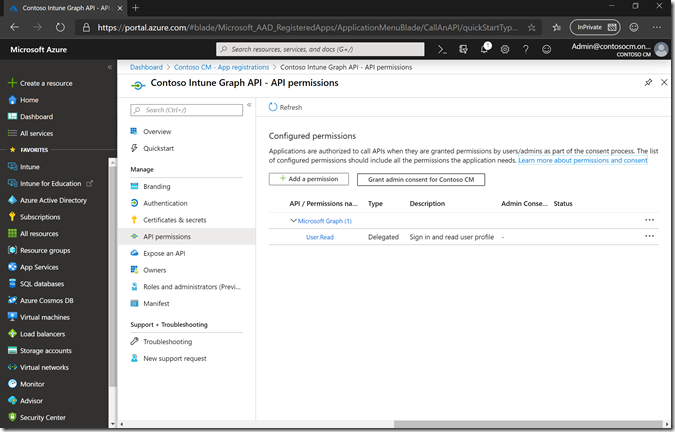
Click on “Microsoft Graph” at the top of the list (not “Intune” further down).
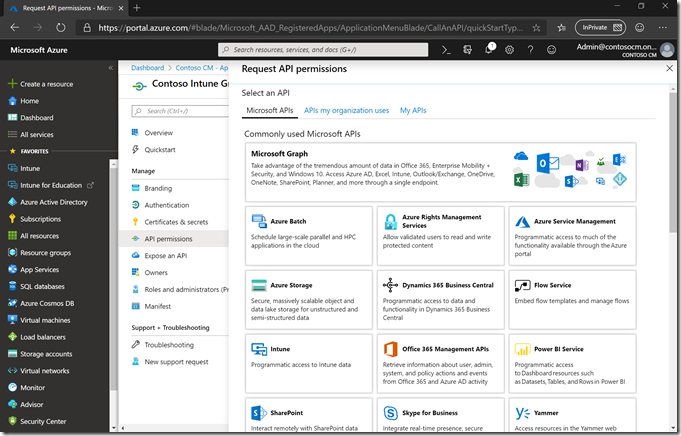
Then choose “Application permissions.”
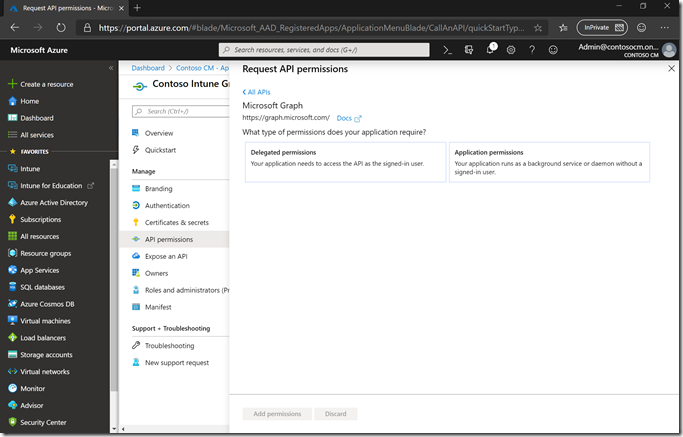
The permission we need for Windows Autopilot are in the “DeviceManagementServiceConfig.ReadWrite.All” permission scope, so select that one:
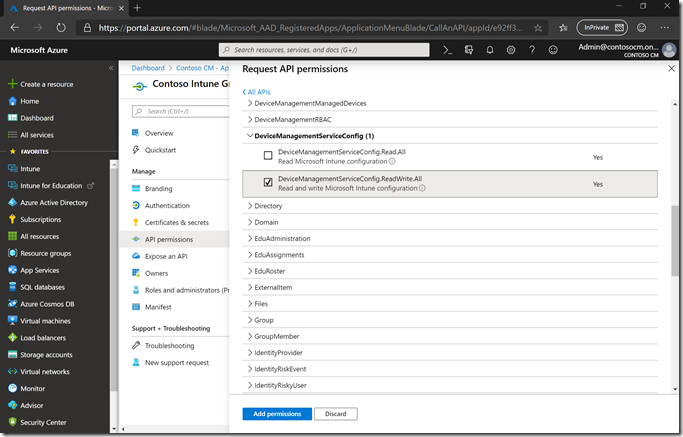
and then click “Add permissions.” After adding it, click the “Grant admin consent” button to enable it.
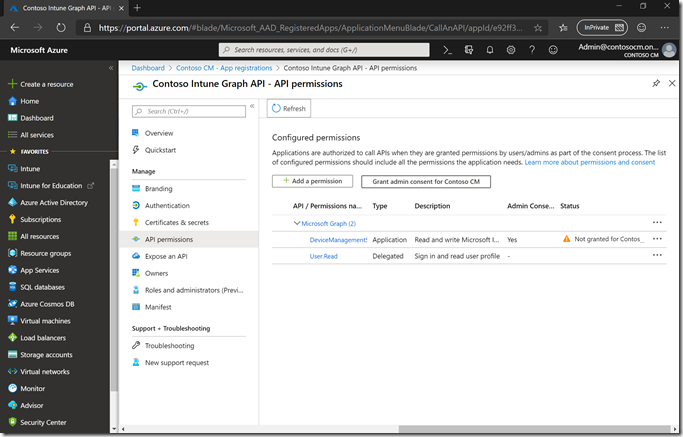
It should then show that it is granted:
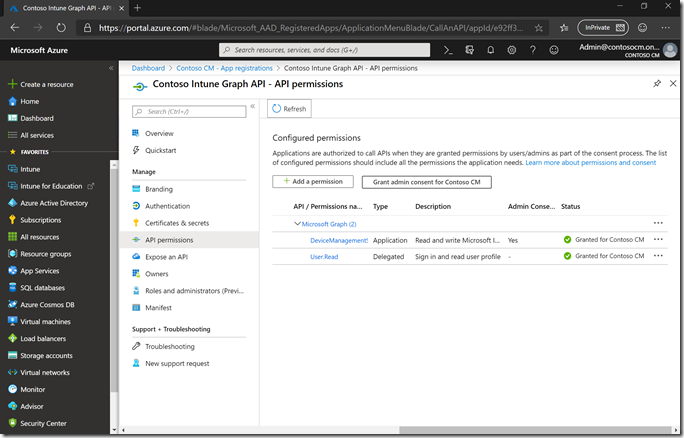
There’s one more thing needed to use the app: We need a client secret for authentication. We can create one of those from the “Certificates & secrets” node. Click the “+ New client secret” button to create one.
You can specify a description and how long it should be valid:
After you click Add, copy the resulting secret to the clipboard – it will be your only opportunity to do so.
Now you can write a script that uses the app. Here’s an example (again with the help of David Falkus):
Import-Module Microsoft.Graph.Intune
Import-Module WindowsAutopilotIntune$tenant = “contosocm.onmicrosoft.com”
$authority = “https://login.windows.net/$tenant”
$clientId = “e92ff304-d681-4ba5-bb42-9683e4bd0d25”
$clientSecret = “<paste your secret here>”Update-MSGraphEnvironment -AppId $clientId -Quiet
Update-MSGraphEnvironment -AuthUrl $authority -Quiet
Connect-MSGraph -ClientSecret $ClientSecret -QuietGet-AutopilotDevice
Note that I didn’t include the actual secret (because it’s like a password and would allow you to access my tenant). If you want to use this script as a starting point, just edit the tenant (you have to explicitly specify what to authenticate against), the client ID (the GUID for the app itself, which can be copied from the Overview page for the app, the “Application (client) ID” value), and the client secret (copied from when you added the secret).
With that script, I can access the tenant with no interaction or credentials, and work with Windows Autopilot devices:
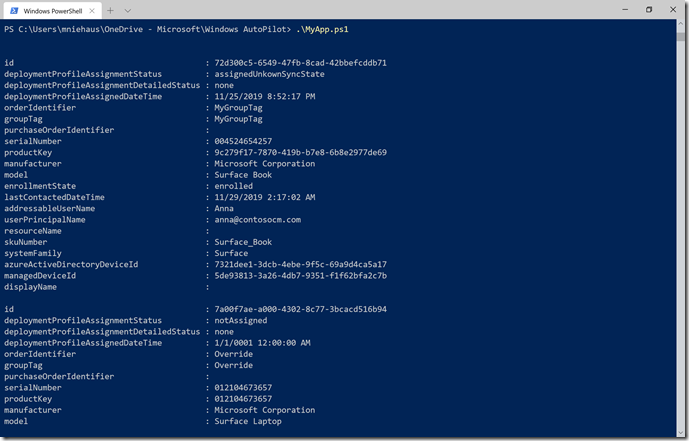
Give it a try yourself.
Categories: Microsoft Intune, Windows Autopilot

I would like to use Get-AutoPilotDevice to query the group tag of a device and pass just the serial number of the device to Get-AutoPilotDevice instead of the -id. But I run into an error if I just pass the -serial. Is there a way to get the -id of the device in through WMI or PowerShell and then pass it on to Get-AutoPilotDevice.
LikeLike
Serial should work as long as it doesn’t have spaces in it (a limitation in the Graph API).
LikeLike
Thanks for your response! I was able to get the group tag info by filtering out the results off Get-AutoPilotDevice based on the serial number. For some reason just executing Get-AutoPilotDevice -serial did not seem to work. I made sure SERIAL did not have spaces within it.
LikeLike