In my past post about the inner workings of UEFI, I talked about using a UEFI shell to poke around, looking at all the UEFI variables that are defined on a typical system. As part of that blog post, I published a PowerShell script to get the value of a particular UEFI variable, but it had some limitations. First, it didn’t let you easily retrieve settings that weren’t strings. And second, it didn’t let you set any variables.
To address those limitations, I created a new PowerShell module published to the PowerShell Gallery called “UEFI.” You can find it here:
https://www.powershellgallery.com/packages/UEFI
Or you can just install it from PowerShell:
Install-Module UEFI
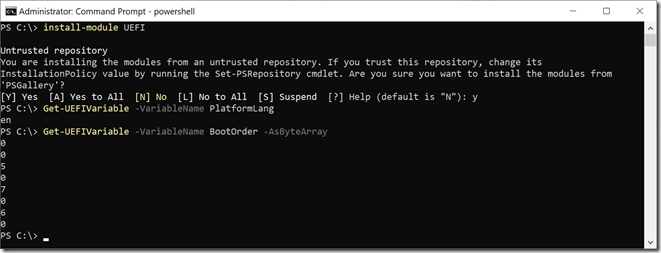
Once installed, you can retrieve some UEFI variables such as those in the examples:
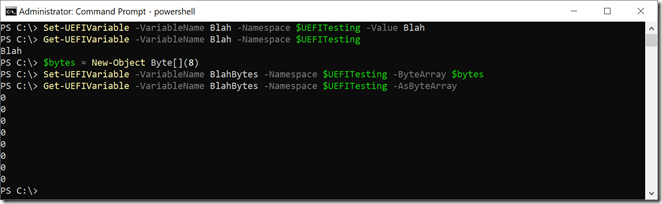
And you can set a variable (in this case, in a namespace that will never get used, but it proves that UEFI will store anything you want):
The only thing you can’t do, because Windows doesn’t include any API calls to enumerate through the available variables, is get a list of UEFI variables that exist on a particular device. Maybe at some point in the future. (Linux provides a way to do this via an efivars file system, which is interesting. But using an EFI shell is easier.)
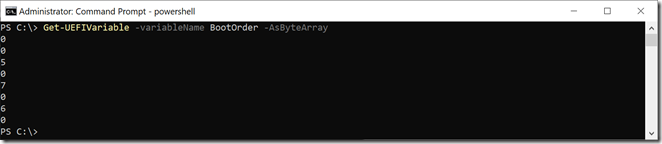
Here’s some extra credit for someone to work on in their spare time: Build a UEFI boot entry editor entirely in PowerShell. It will be a bit tedious to do, because the boot entries are crammed into single variables, but at least the variables are reasonably obvious. First, the “BootOrder” variable give a list of boot entries:
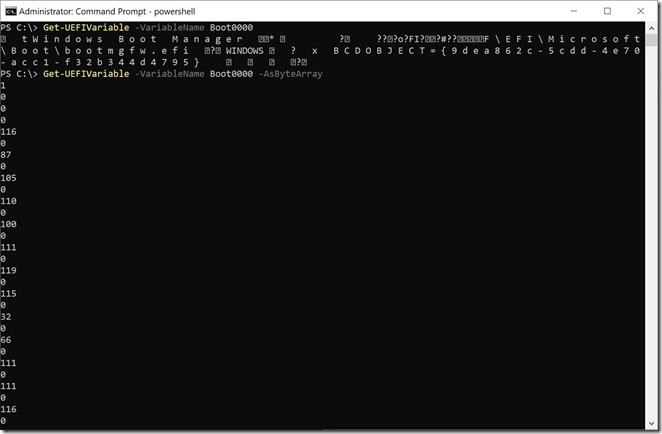
That tells you what BootNNNN entries exist. From the list above, the order is Boot0000, Boot0005, Boot0007, and Boot0006. (The byte order is backwards, so the first byte is the second digit, and the second byte is the first digit.) You can then retrieve each of those boot entries:
The first retrieval as a string shows that there are Unicode strings and other garbage combined into that single variable. The second command then gets you a byte array. The UEFI spec would help you walk through that byte array and split it into individual attributes that together form a boot entry. Good luck with your decoding.
Categories: Windows 10

1 reply »